An alert provides notification of a condition that you are interested in monitoring.
In most cases, this condition is a problem or potential problem that you want to avoid. For example, you may want to get alerts when a server becomes unavailable.
Bradmark Surveillance automates the monitoring process through rules analysis and event generation. From these events, the system determines the actions that need to be taken. The events and the actions performed in response to those events compromise the alerts.
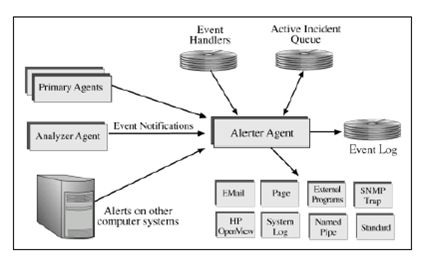
This process begins by defining and applying data rules in the Analyzer Agent. When the agent is started, it loads its rule set, attaches to the appropriate data collections, and begins a continuous process of evaluating rules. If a rule has been satisfied (for example, something noteworthy has occurred) it generates an event that is sent to the local Alerter. The Alerter receives the event, and determines which, if any, Event Handler is appropriate for handling the event. An incident is then created in the Active Incident Queue and performs the actions defined in the Event Handler. When all actions have been completed, the incident is closed.
For example, when defining a rule that informs that the Average Number of New Sessions has exceeded 25, the name of the event is generated by the rule, AVG_NEW_SESSIONS_ EXCEEDED. This rule is then applied, or turned on, for a database. When the database encounters an Average Number of New Sessions that exceeds 25, an event with the Event ID “AVG_NEW_SESSIONS_EXCEEDED” is generated and sent to the Alerter Agent.
In order to handle the event AVG_NEW_SESSION_EXCEEDED, the Alerter Agent will require an event handler to be defined. The event handler might have two actions defined: E-mail and Page the DBA.
If an event handler has no actions defined, then only an incident is opened.
Open incidents are what drive the Alerts Dashboard. The Alerts Dashboard reflects a summary of the open incidents for a given server or entity. For example, if a critical event for low free space arrives, then an incident is opened, and that entity may show as red in the Alerts Dashboard. But once the low free space condition is cleared, then the incident is closed, and the entity may show as green in the Alerts Dashboard.
On a Satellite Server, the only event action defined may be a FORWARD action, to forward all alerts to the Central Alerter Server (CAS). Then, on the CAS, there may be event actions centrally defined, in addition to reflecting open incidents on its Alert Dashboard.